Third-Party Cyber Risk in 2025: Breaches, Insurance Denials, and What CEOs Need to Fix Now
Third-party cyber risks: A leadership blind spot that needs addressing
Let me ask you a simple question:
How many critical issues does it take to sink a business?
If you’ve got 46 vendors (like the company in our dataset) and they’re carrying a combined 487 critical issues… well, let’s just say that’s a lot of exposed electrical wiring under your business floorboards. The kind you don’t notice until someone gets zapped—or sued.
On average, that’s 10.6 critical vulnerabilities per vendor. And that’s just the tip of the spear.
We’re talking about:
- Past breaches with no resolution.
- Ransomware risk that’s edging toward the red.
- Compliance below 75%.
This isn’t a technical problem. This is a leadership blind spot. And CEOs, CFOs, and Business Owners need to fix it, not delegate it into the abyss of IT tickets.
The Reality Behind the Numbers
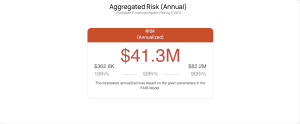
Annualized Risk
That $41.3M number? That’s your probable annualized loss based on external exposure across your third-party footprint. A $362.8K best-case and $82.2M worst-case spread doesn’t exactly scream “manageable.”
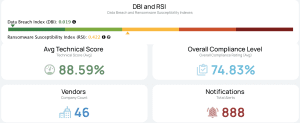
Aggregated Risk for 46 Vendors
- Data Breach Index: 0.019 (low—good!)
- Ransomware Susceptibility Index: 0.422 (yellow trending orange—not good)
- Technical Score: 88.59%
- Compliance: 74.83%
- Total Alerts: 888 (yes, like the number you call when everything’s on fire)
What the Vendor Report Card Shows Us
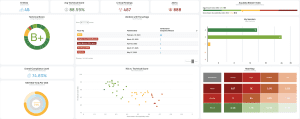
The State of 3rd Party Risk
- 5 vendors flagged for breach-related issues
- 1 vendor still hasn’t addressed a breach from over 2 years ago
- 487 critical findings
- 1,000 high
- 5,500 medium
- 5,900 low
You wouldn’t let someone with 487 health violations cater your daughter’s wedding, right? So why let them manage your sensitive data?
Recent Headlines That Should Keep You Up at Night
- Whole Foods distributor UNFI ransomware attack
- Adidas customer data breach via vendor portal
- LexisNexis breach exposing 364K individuals
These weren’t caused by hackers doing spy movie stunts. They were caused by the digital equivalent of leaving the backdoor open and a sign that says “We’re closed. But not really.”
The Insurance Reality No One Tells You
“We didn’t get breached—but our vendor did. And the insurer still denied the claim.” – CFO, Mid-Market Manufacturer (2024)
Cyber insurance carriers are now evaluating your vendors’ risk posture almost as closely as your own. If a third party causes the breach, and you didn’t vet them? Don’t expect a payout.
What You Can Do (Right Now)
- Know your vendors. Don’t assume your MSP has it covered. Ask for proof.
- Run a 3rd-party risk scan. Think of it like a background check before hiring a babysitter.
- Fix the top 10. You don’t need perfection, you need direction.
- Review your cyber insurance. Hint: They’re watching this stuff now. A bad report can cost you your policy—or your claim.
Bottom Line:
This isn’t just a technical risk—it’s a financial and operational threat that affects your valuation, reputation, and insurance.
Your business isn’t just your business. It’s every vendor, supplier, IT provider, and digital handshake you’ve ever made.
And right now, some of those handshakes are holding live grenades.
P.S. If you’ve read this far and still haven’t asked your CISO (or IT provider) to pull your third-party risk report… I’ve got bad news: You ARE the risk.
📍 Want to get a grip on it? Visit www.ncxgroup.com and let’s talk.
—Mike Fitzpatrick, NCX Group
Let’s Talk
If it’s been more than a year since your last cybersecurity assessment—or if you’ve never done one—now is the time.
👉 Schedule a Strategy Call with NCX Group
Repost from LinkedIn – https://www.linkedin.com/pulse/third-party-cyber-risk-2025-breaches-insurance-what-ceos-fitzpatrick-qip2f/
