
by Maria Florio | Sep 24, 2013 | Blog
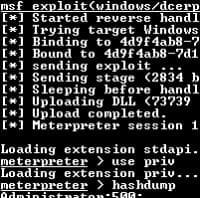
A recent study focusing on the state of risk-based security management has found that only 46 percent of IT professionals have deployed continuous monitoring. Furthermore, many organizations that spend on perceived security risks, have not implemented preventive security technologies, and do not use audits often to identify security risks.
by Maria Florio | Sep 4, 2013 | Blog
In today’s marketplace the most valuable aspect of an organization, and sometimes the only things of value, is the information created, stored, and used to serve their customers and to be able to maintain a competitive advantage over their competitors. Many organizations have realized this and have allocated budget to systems to protect this data. The challenge is this only addresses one-third of the picture.

by Maria Florio | Sep 3, 2013 | Blog
The corporate culture of an organization has a huge impact on the success of your information security plan. It can help build a strong defense or make it weak and filled with vulnerabilities. Three of the biggest challenges organizations and executives face include: the level of threat perceived, location, and lack of cooperation and communication between executives and IT leadership. Overcoming these corporate challenges can help businesses secure their facility.
by Maria Florio | Aug 28, 2013 | Blog
As networks expand and evolve, so do the attack vectors and the need to ensure you do not have any gaps in your network. Furthermore, virtual environments have increased due to the fact that most IT groups have been asked to do more with less. This request comes at a price and IT professionals are worried about the protection of their information assets. Solomon recommends three ways to help reduce and address these concerns.

by Maria Florio | Aug 26, 2013 | Blog
Protecting your facility’s information from breach faces a good deal of challenges. In the past few months various organizations have had their data compromised, like the University of Virginia or the Office of the Medicaid Inspector General. This is a clear statement that institutions and their CIOs are still in great need of a strong information security plan; or for sure that they have yet to establish a security strategy and system to suit their needs.
by Maria Florio | Aug 21, 2013 | Blog
One of the best ways to check the security of your web-based applications is to check the Open Web Security Application Project (OWASP) Top 10 List. The OWASP has been the basis for a security checklist for ten years now. Did you know the OWASP updated their Top 10 list this year? How often do you look for the Top 10 risks in your web-based applications?






