Bite Size Security Blog
Keep your business secure with the latest cybersecurity and information security news from NCX Group. Our team of experts provides you with analysis and insights on potential threats to help protect your enterprise.
Get informed and stay safe with NCX Group.
Bite Size Security Blog
Keep your business secure with the latest cybersecurity and information security news from NCX Group. Our team of experts provides you with analysis and insights on potential threats to help protect your enterprise.
Get informed and stay safe with NCX Group.

Latest Updates
Why security concerns continue to be a huge barrier to cloud adoption
The benefits for business in an increasingly connected world are many, but with those benefits there are also multiple security concerns. The adoption of the cloud is a perfect example of this reality. Recent surveys have shown that one of the reasons for slow adoption of the cloud includes security…
Verizon Report shows that PCI Compliance alone doesn’t work
Verizon’s 2015 PCI Compliance Report shows some good news and bad news regarding businesses and PCI compliance. One of the most important findings is that more organizations are meeting full compliance, but they are not able to sustain compliance long-term making compliance alone ineffective for security…
Gemalto’s breach and response leave security professionals questioning
The recently disclosed Gemalto breach brings heightened concerns to security professionals and organizations alike. According to the published report by The Intercept, Gemalto (a company that operates in 85 countries and has more than 40 manufacturing facilities) was breached by U.S. and U.K. intelligence agencies in 2010.
Anthem Breach: Healthcare organizations continue to struggle with security
The second biggest health insurer in the US, Anthem Inc., suffered a data breach that affected 78.8 million individuals. This is only one of the latest breaches to affect a healthcare provider and is a sign to the industry that something needs to change when it comes to security.
3 steps to get your security on track
With the mega breaches from 2014 and the recent Sony breach, there’s been a huge wake up call for organizations to take risk management seriously. Steps in the right direction are being made, but there’s still a lot more that can be done. Some additional steps executives and security leaders can take…
Security takeaways from the Sony breach
The recent Sony breach is yet another indication of the need for organizations to take security seriously. Business executives keep relying on incomplete risk management solutions, and these are not working. They never worked, and this year’s breaches make this all the more obvious. Don’t you think?
5 steps security executives can implement now to prepare for 2015
A continuously changing threat landscape requires a proactive approach to risk management. New technology tools and skills are only two pieces of the puzzle. Here are 5 additional steps executives can take to secure their network and business in 2015.
Exploring some of the security challenges executives can expect for 2015
After a year of mega breaches, security and business executives can expect an even busier 2015 for cyber risks. With the growth in use of mobile devices and applications in the workplace, plus the IoT boom; enterprise networks have increased their vulnerabilities…
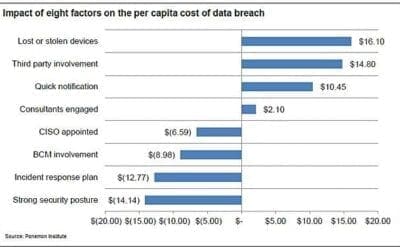
Key Security Takeaways from the Global Report on the Cost of Cyber Crime
Ponemon Institute’s 2014 Global Report on the Cost of Cyber Crime shows some very concerning information for business executives. Not only has cybercrime cost increased, but so has the time required to resolve a cyber attack…
Secure 20/20 – Ebola, Pandemic Plans and Impacts To Your Business
In this Broadcast, NCX Group CEO and Host of Secure 20/20, Mike Fitzpatrick interviews Kathleen Lucy. Kathleen is a Fellow at the Business Continuity Institute and one of the foremost Business Continuity and Cyber Security experts in the world. During our time...
Pandemic plans and key actions to manage the impact of Ebola on your business
If your business continuity managers have been doing their job, you should have an actionable plan set up to manage risks that could arise from unexpected events such as an Ebola outbreak. Unfortunately, this is not always the case; and with the outbreak of Ebola in the U.S., b…
Are privacy and security concerns overrated?
We see individuals somewhat reacting to breach news, but what about organizations and the executive team? It seems the announcements of breach are falling on deaf ears when it comes to them, which makes us wonder if business leaders really care about privacy and what level of privacy do they want to offer their customers?
Tuning out breach news won’t eliminate your security risks
Heightened data breach news coverage could be causing a “tune out” reaction instead of a learning one. For security professionals and business executives this is a detrimental response…
If you think your business security is ready for the IoT, think again
It’s challenging for businesses to keep up with security risks when the growth of connected systems and production of devices are accomplished within a blink of an eye. Even more problematic is the fact that the developers of these technologies are not including security measures during the design and production stage. To give you an idea of what security risks we’re talking about with the IoT and connected devices, OWASP has a helpful top 10 list you can reference…
Security risks just got a whole lot scarier
Another big breach story reminds executives of just how important risk management is for their enterprise. Not only is the recent incident a nightmare for users, but it is also a major indicator that businesses are not securing their site’s databases. A look at what organizations need to know and do to protect customers, intellectual property, and business…
What’s Your Security Why?
As an executive that is fully invested in the growth of your business, have you ever wondered why some businesses succeed while others fail when both have the same potential? The answer is in the “Why.” Why an organization does what they do is what makes them different from other businesses. The same goes for your information security.
Critical infrastructure organizations need to step up their cyber security threat preparedness
Critical infrastructure organizations need to step up their security if they are going to avoid a disastrous situation. A recent Ponemon survey reports that only 17% of companies have fully deployed IT security programs and only 15% find their threat intelligence effective and actionable to stop or minimize the impact of a cyber attack.
Communicating security effectively to the CEO to avoid a business disaster
Businesses are still taking it slow when it comes to security. A recent survey by TrainACE reveals that a majority of organizations are employing best practices; but don’t have the basics set up. One of the biggest challenges is communication between security professionals and the executive team. Learning to speak the CEO’s language on matters of security is a better solution than waiting for breach. Some ways CIOs can close this gap…
2 simple recommendations to avoid an information security nightmare
What can CIOs and CEOs do to avoid Target’s fate? The first step is to realize that information security is not only an IT concern, but also a C-level corporate one because the livelihood of your business depends on how seriously you take your security posture…
What CEOs need to know to avoid Target’s bad security practices and decrease data breach costs
The recently released Ponemon Institute Cost of Data Breach Study shows some concerning information on data breaches that business executives really need to be aware of and take action on through implementing a higher security stance before it’s too late. Not only have breach costs increased, but companies are still lacking when it comes to implementing the necessary risk management components to protect their data and environment.
Don't Be Shy.. Get In Touch.
If you are interested in working together, send us an inquiry and we will get back to you!