Bite Size Security Blog
Keep your business secure with the latest cybersecurity and information security news from NCX Group. Our team of experts provides you with analysis and insights on potential threats to help protect your enterprise.
Get informed and stay safe with NCX Group.
Bite Size Security Blog
Keep your business secure with the latest cybersecurity and information security news from NCX Group. Our team of experts provides you with analysis and insights on potential threats to help protect your enterprise.
Get informed and stay safe with NCX Group.

Latest Updates
Improving communication with leadership to keep your infosec strong
To be successful in any endeavor a business must have fluid and good communication. Communication brings knowledge, awareness and understanding. Without the three, improvements can not be made. This criterion applies to all aspects of your business, including information security. So, what are the leadership problems with communication and full comprehension when it comes to information security?
Taking a proactive approach to your information security needs
A recent Ponemon Institute survey found that 64 percent of IT professionals don’t communicate security risk with senior executives or only communicate them when a serious security risk is revealed. This is detrimental to the security of any business because it puts...
5 hospital security concerns with EHR after Obamacare
Obamacare’s provision requiring medical providers to switch from paper records to electronic health records (EHRs) is intended to reduce costs and help patient care, but it could be happening all too quickly for the proper information security measures to be taken to avoid unwanted access to that data.
Secure 20/20 – The State of Risk Based Security
The State of Risk Based Security Secure 20/20 podcast discusses the new research information from Tripwire and The Ponemon Institute with our guest Dwayne Melancon, CTO of Tripwire, Inc.
Secure 20/20 – Interview with Larry Ponemon
NCX Group CEO and Host of Secure 20/20, Mike Fitzpatrick interviews Dr. Larry Ponemon of the Ponemon Institute. During the interview we discuss Dr. Ponemon's cutting research on Healthcare Privacy and Security, Application Security and the latest research on the Cost...
Reducing infosec costs and breach with continuous monitoring
Do you know what happens when organizations opt to regularly monitor their networks to check the system’s security on an ongoing basis? Find three results from continuous monitoring that all business owners and executives will appreciate; as well as how an enterprise can implement continuous monitoring effectively.
3 Obamacare information security challenges for healthcare
As facilities continue working on their HIPAA compliance requirements, there are more standards executives need to take into consideration and get ready for. This time what affects their everyday work is Obamacare. With Obamacare healthcare data security for individuals and facilities confront at least three challenges: the potential of identity theft, increased risk of vulnerabilities and breach, and breach reporting under HIPAA.
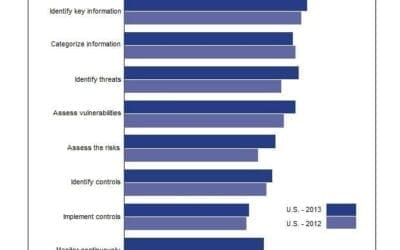
The state of risk-based security management
A recent study focusing on the state of risk-based security management has found that only 46 percent of IT professionals have deployed continuous monitoring. Furthermore, many organizations that spend on perceived security risks, have not implemented preventive security technologies, and do not use audits often to identify security risks.
Organizational Culture and Security
In today’s marketplace the most valuable aspect of an organization, and sometimes the only things of value, is the information created, stored, and used to serve their customers and to be able to maintain a competitive advantage over their competitors. Many organizations have realized this and have allocated budget to systems to protect this data. The challenge is this only addresses one-third of the picture.
How does your corporate culture affect information security?
The corporate culture of an organization has a huge impact on the success of your information security plan. It can help build a strong defense or make it weak and filled with vulnerabilities. Three of the biggest challenges organizations and executives face include: the level of threat perceived, location, and lack of cooperation and communication between executives and IT leadership. Overcoming these corporate challenges can help businesses secure their facility.
Are there gaps in your data protection?
As networks expand and evolve, so do the attack vectors and the need to ensure you do not have any gaps in your network. Furthermore, virtual environments have increased due to the fact that most IT groups have been asked to do more with less. This request comes at a price and IT professionals are worried about the protection of their information assets. Solomon recommends three ways to help reduce and address these concerns.
3 ongoing tasks for the CIO to reduce data breach risks
Protecting your facility’s information from breach faces a good deal of challenges. In the past few months various organizations have had their data compromised, like the University of Virginia or the Office of the Medicaid Inspector General. This is a clear statement that institutions and their CIOs are still in great need of a strong information security plan; or for sure that they have yet to establish a security strategy and system to suit their needs.
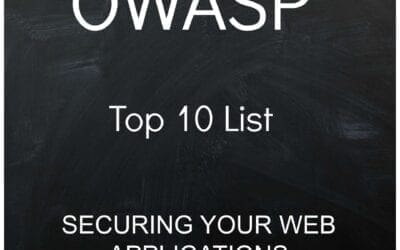
How Secure is Your Web Application?
One of the best ways to check the security of your web-based applications is to check the Open Web Security Application Project (OWASP) Top 10 List. The OWASP has been the basis for a security checklist for ten years now. Did you know the OWASP updated their Top 10 list this year? How often do you look for the Top 10 risks in your web-based applications?
How CIOs can overcome two common information security challenges
The CIO is in charge of various information security areas; this can make it challenging to ensure top security and compliance are met at all times. The challenge doesn’t arise from any lack on the part of the CIO, but it arises from the limited time and resources available to them.
How do cyber security threats affect healthcare facilities?
Due to medical devices being connected to a healthcare facility’s network, when they become vulnerable to cyber security threats and the possibility of infection this creates a risk to the effective operation of the devices (and the facility itself). This risk leads...
3 Things That Keep the CIO Up At Night
The CIO has big responsibilities when it comes to managing a facility’s network security and IT team. Ensuring financial or data losses do not take place are constantly in the forefront of any decision the CIO must make. But what is the breakdown of some of these...
6 steps healthcare facilities take to prepare for OCR audits and meet HIPAA compliance
As most hospital executives and CIOs know, the Office of Civil Rights (OCR) is pushing compliance audits to heighten personal healthcare information (PHI) security measures and avoid data breaches. The Omnibus HIPAA or potential passing of the Executive Orders does...
Preventing data breach and reporting after Omnibus HIPAA
The Omnibus HIPAA breach definition makes it much easier for healthcare organizations’ personal health information (PHI) to become compromised. It also specifies that when data loss or breach happens, it must be reported to the individuals affected, HHS and sometimes,...
The affects of Omnibus HIPAA on healthcare organizations and their information security
The Omnibus HIPAA affects healthcare organizations in three ways: privacy, security, and breach standard and notification; not to mention the HIPAA enforcement rule which applies the increased tiered civil monetary penalty structure of the HITECH Act. The new...
The Watch Dog Report – Business Continuity 101
Interview with NCX Group's own and Business Continuity Institute Fellow Doug Weldon, is from the Best of The Watchdog Report. During the interview we discuss the importance of Business Continuity in addressing Information Risk Management. By the end of this interview...
Don't Be Shy.. Get In Touch.
If you are interested in working together, send us an inquiry and we will get back to you!