


Security takeaways from the Heartbleed bug incident
In addition to creating agitation and giving intruders a way to gain access to sensitive data, the Heartbleed bug incident has also served as an additional nudge to businesses regarding their security posture. A look at some of the important takeaways for security professionals and executives from the Heartbleed vulnerability incident can help…

What CIOs need to keep in mind with the Internet of Things and information security
CIOs are already under a lot of pressure when it comes to information security. The IoT boom will only increase this responsibility, which means more resources and enough manpower to implement the necessary level of risk management actions are required. Some of the challenges and solutions you should keep in mind to secure your business…
Reducing infosec costs and breach with continuous monitoring
Do you know what happens when organizations opt to regularly monitor their networks to check the system’s security on an ongoing basis? Find three results from continuous monitoring that all business owners and executives will appreciate; as well as how an enterprise can implement continuous monitoring effectively.

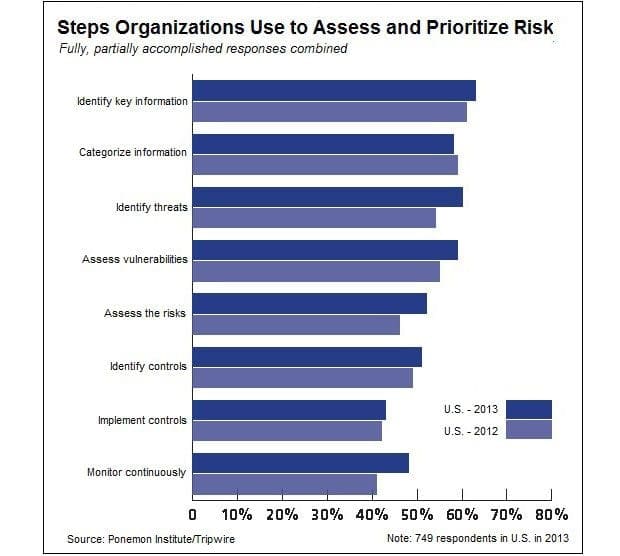
The state of risk-based security management
A recent study focusing on the state of risk-based security management has found that only 46 percent of IT professionals have deployed continuous monitoring. Furthermore, many organizations that spend on perceived security risks, have not implemented preventive security technologies, and do not use audits often to identify security risks.
